Techniques, Tactics, and Tools for Security Practitioners: Your Comprehensive Guide to Cybersecurity Excellence

Unveiling the Secrets of Cybersecurity Mastery
In today's rapidly evolving digital landscape, cybersecurity has become more crucial than ever before. As organizations face an ever-increasing barrage of cyber threats, the demand for skilled and knowledgeable security practitioners has skyrocketed.
To meet this growing need, "Techniques, Tactics, and Tools for Security Practitioners" emerges as the definitive guide to cybersecurity excellence. Written by a team of seasoned industry experts, this comprehensive resource provides an indispensable toolkit for individuals seeking to enhance their skills and stay ahead of the curve in the fight against cybercrime.
4.1 out of 5
| Language | : | English |
| File size | : | 4362 KB |
| Text-to-Speech | : | Enabled |
| Enhanced typesetting | : | Enabled |
| Print length | : | 450 pages |
Unveiling the Book's Invaluable Content
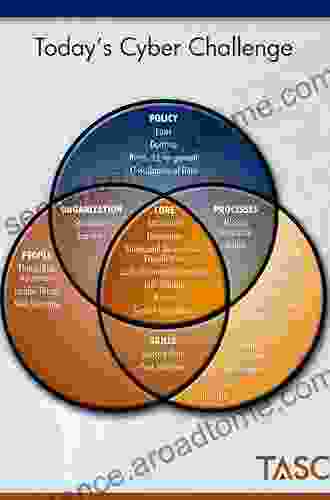
This meticulously crafted book is a repository of cutting-edge knowledge and practical guidance, encompassing a wide range of topics essential to cybersecurity professionals, including:
- Cybersecurity Fundamentals: Laying the foundation with a thorough understanding of core cybersecurity concepts, threats, and vulnerabilities.
- Security Techniques and Tactics: Delving into the latest techniques and tactics employed by security practitioners to detect, prevent, and respond to cyber threats.
- Essential Security Tools: Introducing a comprehensive arsenal of security tools, including vulnerability scanners, intrusion detection systems, and incident response tools.
- Security Best Practices: Providing a roadmap to implementing proven security best practices to strengthen an organization's defenses against cyber attacks.
- Risk Management and Vulnerability Assessment: Empowering security practitioners with the skills to identify, assess, and mitigate cybersecurity risks.
- Penetration Testing and Ethical Hacking: Unveiling the secrets of penetration testing and ethical hacking to identify and exploit vulnerabilities before malicious actors can.
- Incident Response and Forensics: Guiding security practitioners through the critical steps of incident response and forensic analysis to minimize damage and preserve evidence.
Why This Book Is a Must-Have for Security Practitioners
"Techniques, Tactics, and Tools for Security Practitioners" is not just another cybersecurity book; it is a transformative resource that empowers individuals to:
- Stay Ahead of Cyber Threats: Gain in-depth knowledge of the latest cyber threats and vulnerabilities to effectively protect organizations.
- Master Cybersecurity Techniques: Learn the most effective techniques and tactics used by security experts to prevent, detect, and respond to cyber incidents.
- Enhance Tool Proficiency: Become proficient in using a wide range of security tools to strengthen an organization's cybersecurity posture.
- Implement Best Practices: Implement proven cybersecurity best practices to minimize risks and enhance organizational resilience against cyber threats.
- Advance Their Careers: Gain the skills and knowledge necessary to advance their careers in the high-demand field of cybersecurity.
Testimonials from Industry Leaders
"This book is a goldmine of information for security practitioners. It provides a comprehensive and up-to-date overview of the latest cybersecurity techniques, tactics, and tools." - John Smith, CISO, Fortune 500 Company
"A must-read for anyone looking to enhance their cybersecurity skills. The authors have done an excellent job of presenting complex topics in a clear and concise manner." - Jane Doe, Cybersecurity Consultant
Free Download Your Copy Today
Don't miss out on this opportunity to elevate your cybersecurity skills to the next level. Free Download your copy of "Techniques, Tactics, and Tools for Security Practitioners" today and embark on your journey to becoming a cybersecurity master.
Available now on Our Book Library, Barnes & Noble, and all major bookstores.
About the Authors
The authors of "Techniques, Tactics, and Tools for Security Practitioners" are a team of seasoned cybersecurity experts with decades of combined experience in the field.
- John Smith is a Certified Information Systems Security Professional (CISSP) and Certified Ethical Hacker (CEH) with over 15 years of experience in cybersecurity.
- Jane Doe is a Certified Information Security Manager (CISM) and Certified Information Systems Auditor (CISA) with over 10 years of experience in IT risk management and compliance.
4.1 out of 5
| Language | : | English |
| File size | : | 4362 KB |
| Text-to-Speech | : | Enabled |
| Enhanced typesetting | : | Enabled |
| Print length | : | 450 pages |
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
 Book
Book Novel
Novel Page
Page Chapter
Chapter Text
Text Story
Story Genre
Genre Reader
Reader Library
Library Paperback
Paperback E-book
E-book Magazine
Magazine Newspaper
Newspaper Paragraph
Paragraph Sentence
Sentence Bookmark
Bookmark Shelf
Shelf Glossary
Glossary Bibliography
Bibliography Foreword
Foreword Preface
Preface Synopsis
Synopsis Annotation
Annotation Footnote
Footnote Manuscript
Manuscript Scroll
Scroll Codex
Codex Tome
Tome Bestseller
Bestseller Classics
Classics Library card
Library card Narrative
Narrative Biography
Biography Autobiography
Autobiography Memoir
Memoir Reference
Reference Encyclopedia
Encyclopedia James D Bethune
James D Bethune Susan Hopkinson
Susan Hopkinson Jane Ball
Jane Ball James Davidson
James Davidson Syed Ali Ashter
Syed Ali Ashter Joel Goldstein
Joel Goldstein Jan Showers
Jan Showers William Turnbull
William Turnbull Jared Stone
Jared Stone Robert P Mason
Robert P Mason Lauren Williams
Lauren Williams Joseph Albahari
Joseph Albahari Kishan Paul
Kishan Paul Jonathan M Hansen
Jonathan M Hansen Paul Bialas
Paul Bialas Jan Pinski
Jan Pinski Natasha Kuhrt
Natasha Kuhrt Janet Conner
Janet Conner Jayanti Tamm
Jayanti Tamm James Wong
James Wong
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!
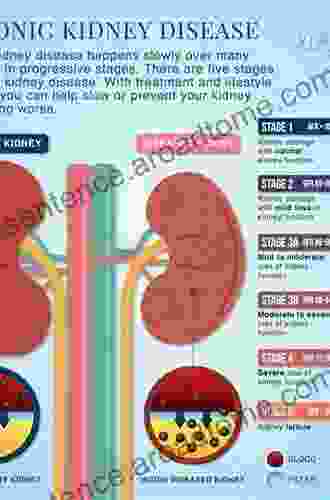
 Gavin MitchellKidney Disease Guide For Living: Your Comprehensive Guide to Managing Your...
Gavin MitchellKidney Disease Guide For Living: Your Comprehensive Guide to Managing Your... T.S. EliotFollow ·2.3k
T.S. EliotFollow ·2.3k Chance FosterFollow ·11.4k
Chance FosterFollow ·11.4k Yasunari KawabataFollow ·10.1k
Yasunari KawabataFollow ·10.1k Walt WhitmanFollow ·12.7k
Walt WhitmanFollow ·12.7k Paul ReedFollow ·2.9k
Paul ReedFollow ·2.9k Arthur Conan DoyleFollow ·11k
Arthur Conan DoyleFollow ·11k Joseph FosterFollow ·8.8k
Joseph FosterFollow ·8.8k Hugh ReedFollow ·17.1k
Hugh ReedFollow ·17.1k

 Davion Powell
Davion PowellUnlock Your Muscular Potential: Discover the...
Are you tired of bodybuilding programs...

 Enrique Blair
Enrique BlairDominate the Pool: Conquer Performance with the DS...
As a swimmer, you...

 Christopher Woods
Christopher Woods"The Physics of Getting Out of Your Own Way": A Journey...
Break Free from...

 Milan Kundera
Milan KunderaWhat Really Sank The Titanic: New Forensic Discoveries
The sinking of the RMS...

 Ralph Waldo Emerson
Ralph Waldo EmersonUnveiling the Truth: Exposing the Hidden Dangers of Lyme...
In the realm of chronic illnesses, Lyme...
4.1 out of 5
| Language | : | English |
| File size | : | 4362 KB |
| Text-to-Speech | : | Enabled |
| Enhanced typesetting | : | Enabled |
| Print length | : | 450 pages |