Unleash the Power of Secure Continuous Delivery: A Comprehensive Guide to Enabling Security in Your Pipeline

In the fast-paced world of software development, continuous delivery (CD) has emerged as a game-changer, enabling teams to deliver high-quality software faster and more efficiently. However, without proper security measures in place, CD pipelines can become a breeding ground for vulnerabilities and security breaches.
4.4 out of 5
| Language | : | English |
| File size | : | 2337 KB |
| Text-to-Speech | : | Enabled |
| Enhanced typesetting | : | Enabled |
| Print length | : | 554 pages |
| Screen Reader | : | Supported |
This comprehensive guide, "Enabling Security in Continuous Delivery Pipeline," is your ultimate resource for integrating security into every stage of your CD process. Written by renowned security experts with extensive experience in DevOps and secure software development, this book provides an actionable roadmap for safeguarding your software from its inception to deployment.
Chapter 1: The Importance of Secure Continuous Delivery
Kick off your journey by understanding the critical role of security in continuous delivery. This chapter explores the benefits and challenges of integrating security into your pipeline, emphasizing the need for a proactive approach to protect against evolving threats. You'll learn how secure CD can mitigate risks, enhance software quality, and boost customer trust.
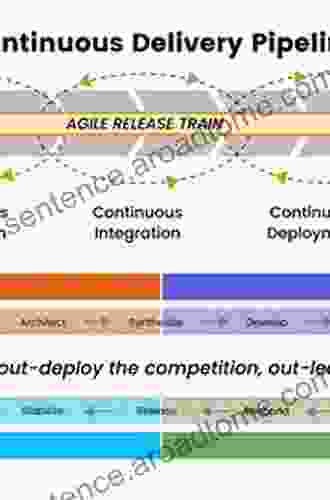
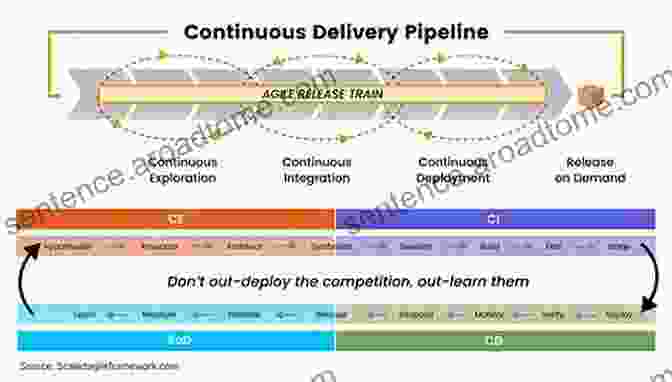
Chapter 2: Security Considerations in CI/CD Pipelines
Delve into the intricacies of implementing security throughout your CI/CD pipeline. This chapter provides a detailed analysis of each stage, identifying potential security gaps and offering practical solutions to address them. You'll explore best practices for code scanning, security testing, vulnerability management, and incident response, equipping you with a comprehensive security strategy.
Chapter 3: Threat Modeling for Secure Software Development
Uncover the importance of threat modeling in designing secure software systems. This chapter guides you through the process of identifying and analyzing threats, developing mitigation strategies, and incorporating security controls into your software architecture. You'll learn techniques for threat elicitation, risk assessment, and attack surface reduction, empowering you to build software that is resilient against malicious actors.
Chapter 4: Automating Security in the CD Pipeline
Maximize efficiency and minimize security risks by implementing automation in your CD pipeline. This chapter demonstrates how to use security automation tools to automate security testing, vulnerability scanning, policy enforcement, and incident response. You'll explore industry-leading security automation frameworks, enabling your teams to focus on delivering value rather than manual security tasks.
Chapter 5: Integrating Security in DevOps Culture
Foster a culture of security within your DevOps team to ensure continuous adherence to security best practices. This chapter explores the key principles of DevSecOps, emphasizing the importance of collaboration, communication, and shared responsibility. You'll learn how to integrate security into your DevOps processes, training, and documentation, creating a culture that values and prioritizes security.
Chapter 6: Measuring and Improving Security in the CD Pipeline
Track and continuously improve the security posture of your CD pipeline. This chapter introduces metrics and dashboards for measuring security effectiveness, highlighting key performance indicators (KPIs) to monitor and optimize. You'll learn how to analyze security data, identify trends, and implement data-driven decisions to enhance your security posture.
Chapter 7: Case Studies and Best Practices
Gain valuable insights from real-world case studies of successful security integrations in CD pipelines. This chapter showcases how leading organizations have overcome common challenges and implemented innovative security solutions. You'll learn from their experiences, best practices, and lessons learned, enabling you to make informed decisions for your own organization.
"Enabling Security in Continuous Delivery Pipeline" empowers you with the knowledge and tools to build and maintain secure software systems throughout your CD pipeline. By integrating security into every stage of the development process, you can deliver high-quality, secure software faster, with reduced risks and enhanced customer trust.
Don't compromise on security in the pursuit of speed and efficiency. Embrace the power of secure CD today and unlock the full potential of your software delivery process.
Free Download your copy of "Enabling Security in Continuous Delivery Pipeline" today and embark on a journey to secure your software development pipeline.
4.4 out of 5
| Language | : | English |
| File size | : | 2337 KB |
| Text-to-Speech | : | Enabled |
| Enhanced typesetting | : | Enabled |
| Print length | : | 554 pages |
| Screen Reader | : | Supported |
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
 Book
Book Novel
Novel Page
Page Chapter
Chapter Text
Text Story
Story Genre
Genre Reader
Reader Library
Library Paperback
Paperback E-book
E-book Magazine
Magazine Newspaper
Newspaper Paragraph
Paragraph Sentence
Sentence Bookmark
Bookmark Shelf
Shelf Glossary
Glossary Bibliography
Bibliography Foreword
Foreword Preface
Preface Synopsis
Synopsis Annotation
Annotation Footnote
Footnote Manuscript
Manuscript Scroll
Scroll Codex
Codex Tome
Tome Bestseller
Bestseller Classics
Classics Library card
Library card Narrative
Narrative Biography
Biography Autobiography
Autobiography Memoir
Memoir Reference
Reference Encyclopedia
Encyclopedia Janice K Ledford
Janice K Ledford Sabina E Deitrick
Sabina E Deitrick Janine Pipe
Janine Pipe Rowan Kaiser
Rowan Kaiser James Fox
James Fox Jeff Kinley
Jeff Kinley T J English
T J English Tiffany Y P
Tiffany Y P Jane Whelen Banks
Jane Whelen Banks Jeff Hwang
Jeff Hwang Janet Lawler
Janet Lawler Jassy Mackenzie
Jassy Mackenzie Marianne J Legato
Marianne J Legato Jason Krol
Jason Krol Kalampedia Publications
Kalampedia Publications Jennifer Carrasco
Jennifer Carrasco Jean Pierre Hugot
Jean Pierre Hugot Joe Atikian
Joe Atikian Jason Chin
Jason Chin Paulette Jiles
Paulette Jiles
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!

 Boris PasternakThe Complete Guide to Narcissism: Unraveling the Enigma of Narcissistic...
Boris PasternakThe Complete Guide to Narcissism: Unraveling the Enigma of Narcissistic...
 Fletcher MitchellUnleash Your True Potential: Master the Art of Resisting Temptations,...
Fletcher MitchellUnleash Your True Potential: Master the Art of Resisting Temptations,...
 Truman CapoteThe Introvert's Guide to Making a Difference: Unlocking Your Potential to...
Truman CapoteThe Introvert's Guide to Making a Difference: Unlocking Your Potential to... Hamilton BellChemical Mechanical Planarization: A Comprehensive Guide to Semiconductor...
Hamilton BellChemical Mechanical Planarization: A Comprehensive Guide to Semiconductor... August HayesFollow ·3.5k
August HayesFollow ·3.5k W.H. AudenFollow ·14.6k
W.H. AudenFollow ·14.6k Tom ClancyFollow ·15.1k
Tom ClancyFollow ·15.1k Sean TurnerFollow ·3.7k
Sean TurnerFollow ·3.7k Jay SimmonsFollow ·4k
Jay SimmonsFollow ·4k Jake CarterFollow ·6.4k
Jake CarterFollow ·6.4k Robert FrostFollow ·14.5k
Robert FrostFollow ·14.5k Dylan HayesFollow ·12.1k
Dylan HayesFollow ·12.1k

 Davion Powell
Davion PowellUnlock Your Muscular Potential: Discover the...
Are you tired of bodybuilding programs...

 Enrique Blair
Enrique BlairDominate the Pool: Conquer Performance with the DS...
As a swimmer, you...

 Christopher Woods
Christopher Woods"The Physics of Getting Out of Your Own Way": A Journey...
Break Free from...

 Milan Kundera
Milan KunderaWhat Really Sank The Titanic: New Forensic Discoveries
The sinking of the RMS...

 Ralph Waldo Emerson
Ralph Waldo EmersonUnveiling the Truth: Exposing the Hidden Dangers of Lyme...
In the realm of chronic illnesses, Lyme...
4.4 out of 5
| Language | : | English |
| File size | : | 2337 KB |
| Text-to-Speech | : | Enabled |
| Enhanced typesetting | : | Enabled |
| Print length | : | 554 pages |
| Screen Reader | : | Supported |